Privacy on Ethereum
Privacy on Ethereum
A comprehensive map of the ongoing projects that are contributing to the development of privacy on the Ethereum ecosystem.
Intro
During EthCC, Anna Rose and Will Harborne, the founders of our ZK Validator, delivered a presentation on the development of privacy in Ethereum. This article is a follow-up to their talk, delving deeper into the privacy ecosystem of the network. It highlights the various players involved, as well as relevant research that has been published and upcoming advancements.
Disclaimer: Please note that this article is not intended as an endorsement for any of the projects mentioned.
Is privacy the same as ZK?
Before delving into Ethereum’s privacy ecosystem, it’s crucial to clarify some terms. Over the past two years, numerous “ZK” scaling solutions have emerged, including rollups and bridges.
Most of these solutions take advantage of the succinctness properties of zkSNARKs, a property that enables blockchains to scale but doesn’t enable privacy. Consequently, the majority of scaling solutions don’t offer privacy preservation capabilities, despite using ZK in their naming conventions and communications.

Other privacy-preserving technologies, such as Trusted Execution Environments (TEEs), Multi-party Computation (MPC) and Homomorphic Encryption (HE) exist, however Zero Knowledge Proofs remain at the forefront of privacy due to their trustless nature.
With that said, we will explore several privacy solutions in the Ethereum ecosystem, including those which use ZK as well as others that rely on different techniques.
What are the current privacy use cases on Ethereum?
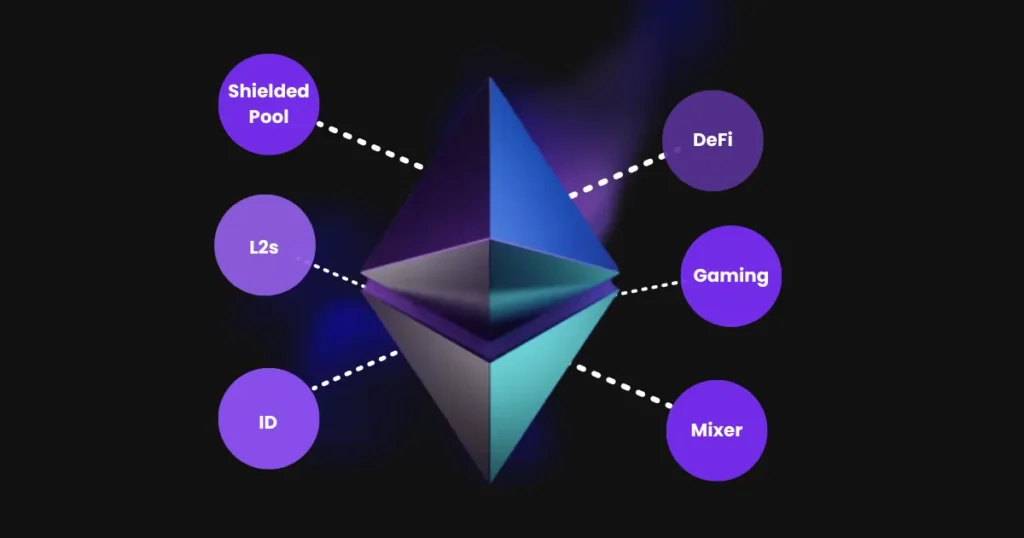
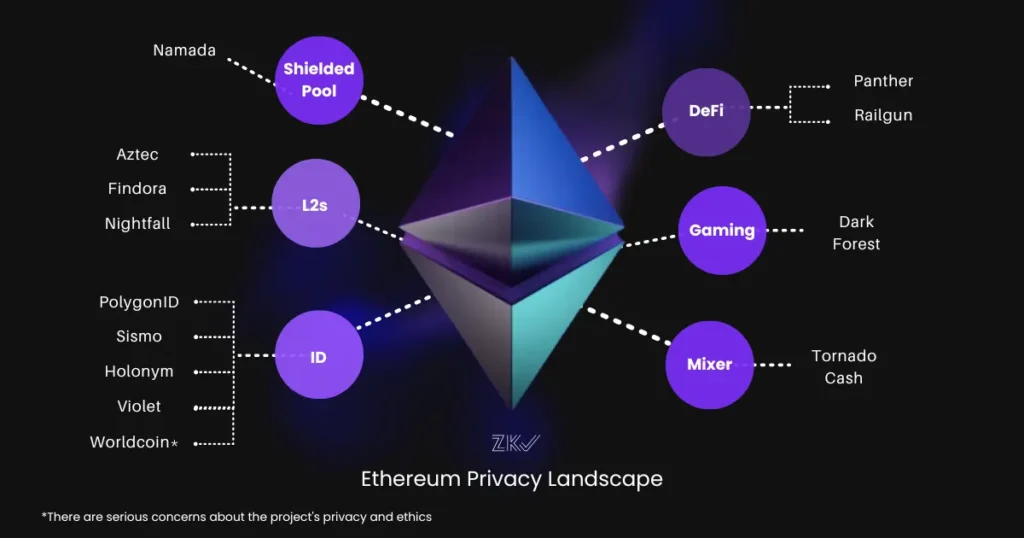
It’s not a secret that the main use case for blockchains is decentralized finance (DeFi). Concurrently, the main use case for privacy apps is private transfers. However, during our research, we found out that the Decentralized Identification segment is one of the fastest-growing niches across the whole privacy ecosystem on Ethereum.
Nevertheless, there are other use cases we will explore such as private computation, gaming, private voting and ZKML.
Private transfers on Ethereum
In this section, we will discuss projects that focus on ensuring privacy in peer-to-peer transfers. There are two categories for this use case: mixers and dApps. Although they both serve the same purpose, the way they ensure privacy differs.
Mixers
Mixers are privacy-enhancing services in the blockchain context that increase transaction anonymity. They achieve this by combining multiple cryptocurrency inputs from different users, shuffling and delaying transactions, and distributing outputs to different addresses than the originals, making it difficult to trace funds on the blockchain and obscures the link between sender and recipient addresses.
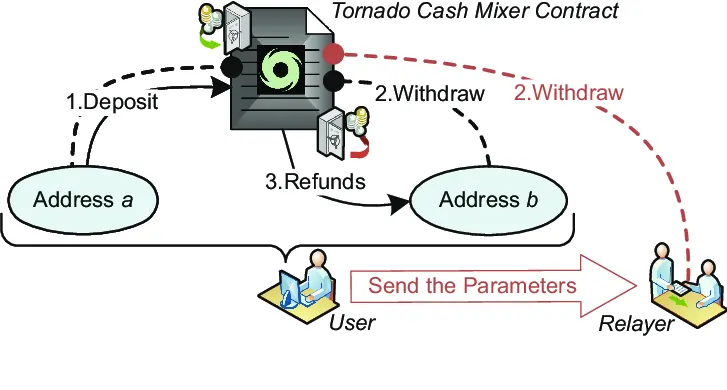
The level of privacy mixers provide depends on their trust model. Centralized mixers require users to trust the service operator not to misuse data, while decentralized mixers use cryptographic protocols to achieve privacy without relying on a central entity.
- Tornado Cash: is a zkSNARK-based mixer. However, it has lost relevance due to being sanctioned by the OFAC. Currently, there are no other significant mixers in the Ethereum ecosystem.
Layer 2s
However, alternative solutions for private transfers do not require using a mixer. Indeed, the trend for enabling private transfers is currently focused on L2 solutions. Below are some of the L2s that have this use case enabled:
Findora: Findora ZK is a privacy-focused layer-2 solution for Ethereum, leveraging Ethereum for consensus and validation. It uses succinct non-interactive arguments of knowledge (SNARKs) in an Ethereum smart contract on layer 1 to validate state transitions and ensure the correctness of the rollup. The layer-2 ledger provides privacy for payments, similar to Findora OG, and enables interoperability with Ethereum using zero-knowledge proofs, allowing for private transfers and confidential transaction data.
Aztec: This is an upcoming L2 offering public and private smart contract execution. Within the L2, developers can offer private transfers thanks to using zkSNARKs. Aztec is called to be the first programmable privacy rollup on Ethereum. They are moving away from the common EVM design, using their own language Noir, in order to make programmable privacy possible for dApps builders.
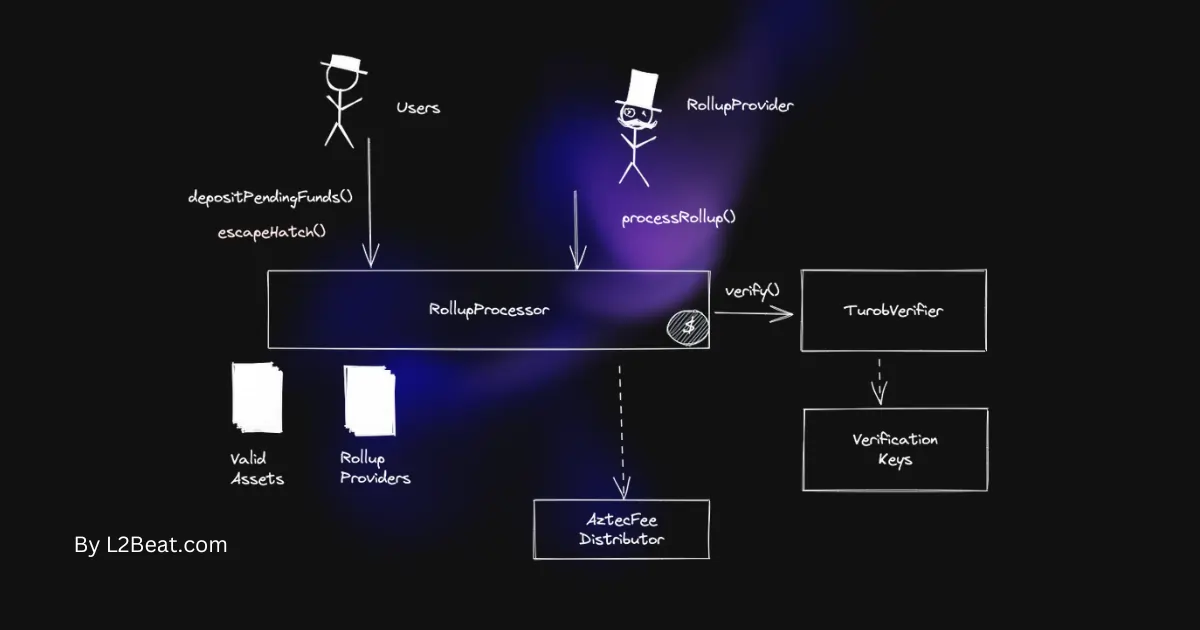
Nightfall: It’s an “zk-optimistic rollup” designed by Ernest & Young with the collaboration of Polygon. It utilizes zero-knowledge proofs (ZKPs) to keep transaction information confidential, making it suitable for business payments while using fraud proofs for correctness.
Private Layer 1 (Shielded Pool)
- Namada: is a proof-of-stake L1 for interchain asset-agnostic privacy. Namada interoperates with Cosmos chains via IBC and with Ethereum via a trust-minimized bridge. Namada gives the privacy landscape a different shape, by providing the largest possible unified privacy set in the multichain, and complementing other chains by seeding/retrofitting privacy shielded actions All assets share one anonymity set, enhancing privacy guarantees.
Privacy Preserving dApps
Private ID
Indeed, there is an emergence of applications dedicated to providing privacy for ID on Ethereum. All of them try to solve the issue of online fragmented identities while preserving the control and privacy of personal information.
Although there are a handful more of applications working with DIDs, the ones using ZKPs to preserve privacy are:
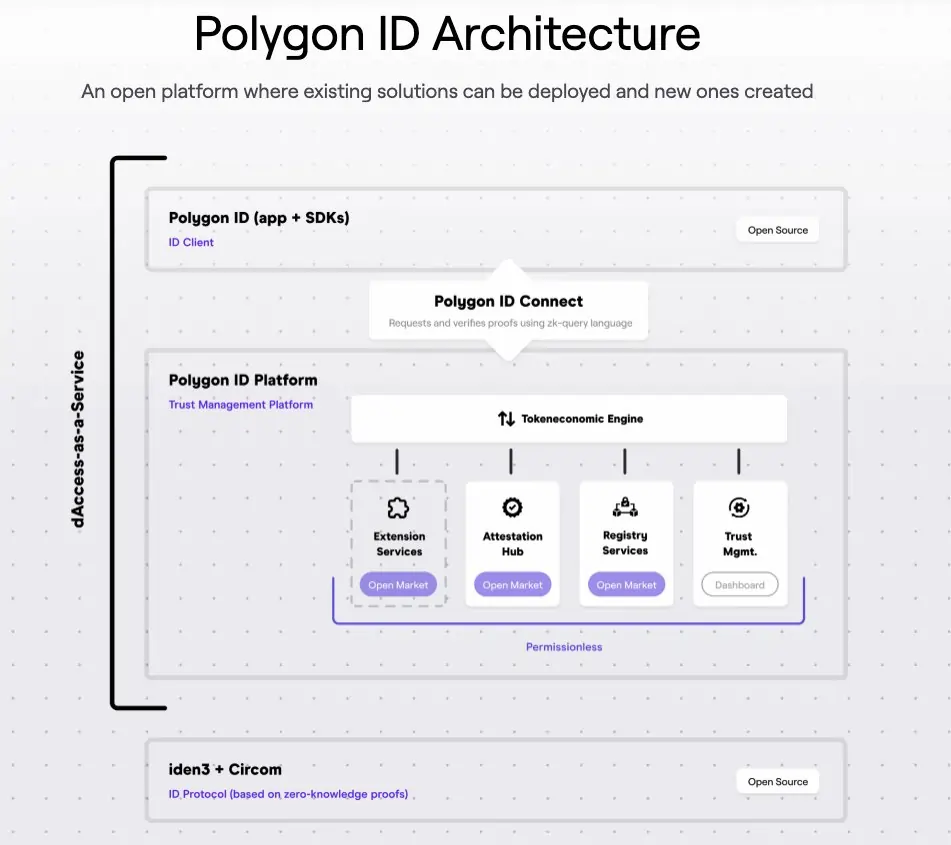
PolygonID: this platform’s foundation lies in expressible claim standards offering distinct advantages over non-fungible tokens (NFTs) and verifiable credentials (VCs), which have limited expressibility and composability, hindering their applicability. Polygon ID’s use of the Circom ZK toolkit enables the compilation of zero-knowledge cryptographic constructions, known as zkSNARKs circuits, reducing complexity and boosting efficiency. Polygon ID offers on-chain verification, which allows for private and trustless execution of user interactions without relying on intermediaries.
Sismo: Sismo is a platform that utilizes zero knowledge proofs (ZKPs) and privacy-preserving technologies to give users greater authority over their personal data. The heart of Sismo’s solution is Sismo Connect, which provides a smooth single sign-on (SSO) process, allowing users to selectively disclose personal data to applications while maintaining privacy.
Worldcoin: the project aims to prevent the proliferation of bots and AI by verifying human uniqueness through an iris scan that is encrypted and stored on-chain. When required, the system generates a ZKP to confirm identity. The project has received scrutiny from community members concerned about privacy, ethics, and security risks associated with the storage of biometric data.
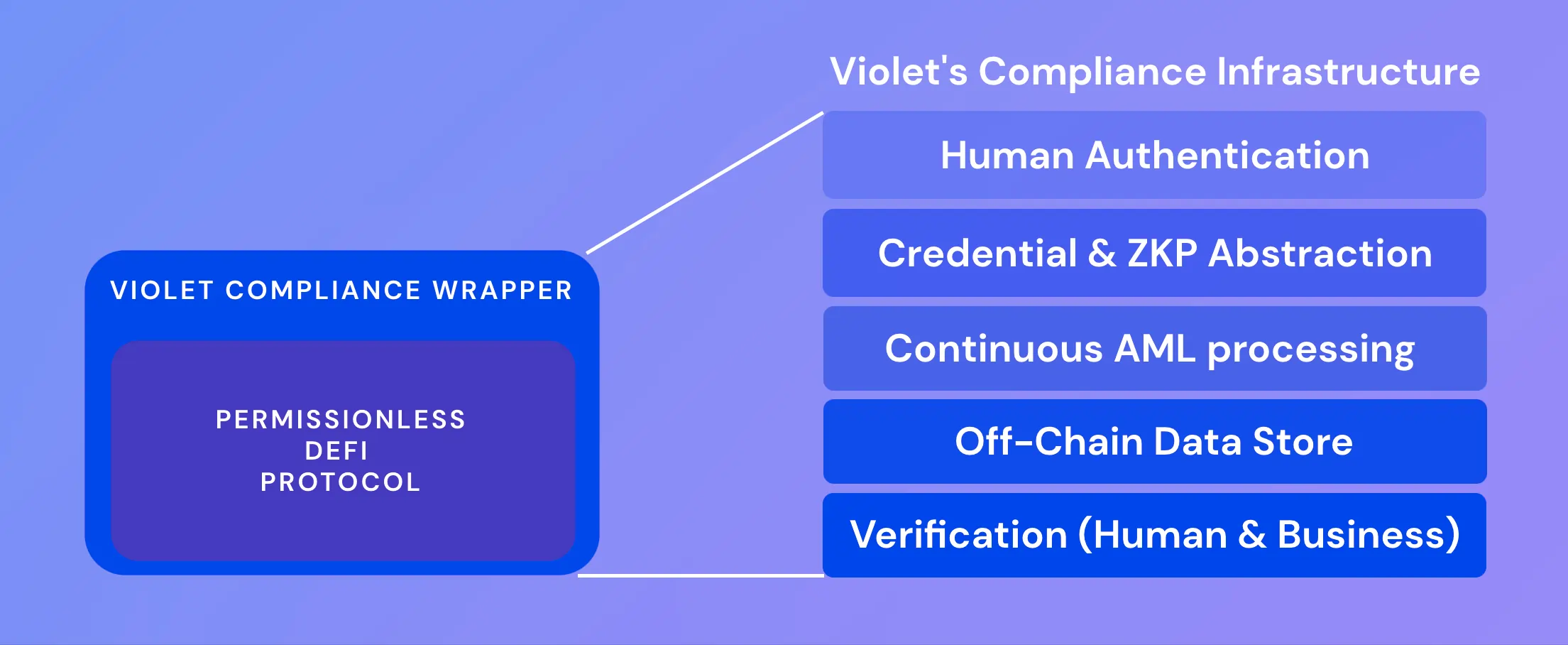
Violet: is a set of compliance and identity infrastructure rails that offer customization options. It provides standardized methods to issue compliance credentials specific to individual transactions, enabling permissioned on-chain function calls for authorized participants only. Violet prioritizes data privacy and sovereignty and avoids storing personally identifiable information on-chain. The described flows and mechanisms fit into a larger, generalizable framework suitable for supporting various compliance regimes, including identity proofing requirements like Humanbound. Violet aims to function as an Ethereum network equivalent of OAuth-like functionality.
Holonym: Holonym functions as an identity bridge and mixer, concealing off-chain credentials and making them accessible on-chain for various web applications. This integration of composable ledgers, privacy-enhancing techniques, and zero knowledge proofs enables a wide range of use cases, including on-chain identity verification, Sybil resistance, digital crime prevention, and noncustodial wallet recovery. These features have implications for the web3 ecosystem and may also have the potential to enhance security and privacy on the wider internet, addressing issues such as crime, Sybil attacks, and data leaks.
Private computation
Decentralized private computation (DPC) is an advanced paradigm revolutionizing data processing and computations in distributed networks.
• DPC enables secure and private data processing across multiple nodes, keeping data under the control of its owners and ensuring confidentiality.
• This allows for secure collaboration, data sharing, and computation in a trustless and privacy-preserving manner.
Additionally, integrating smart contracts enhances DPC capabilities, enabling transparent and automated execution of predefined tasks with strong privacy guarantees through cryptographic protocols and zero-knowledge proofs.
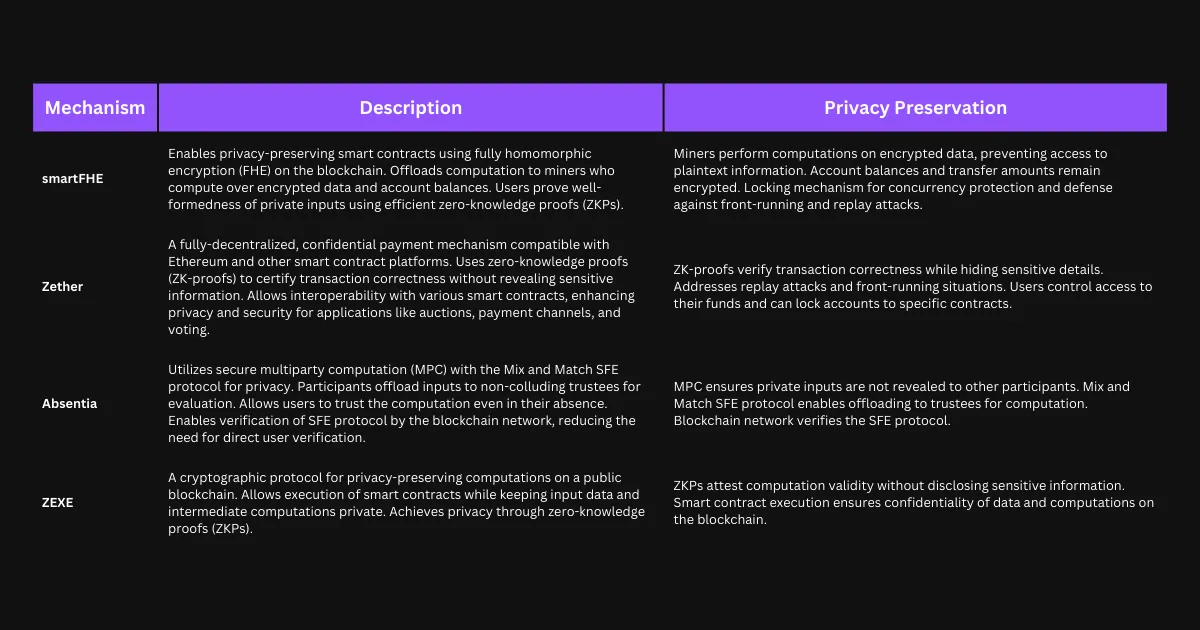
Within the Ethereum network, there are two significant initiatives focused on this objective: Aztec and Polygon Maiden. Additionally, there have been notable research papers published in this field, including the following breakthroughs:
Private Voting
There have been recent voting proposals which caused debates and controversies in various communities. In some instances, people have attempted to bribe or dissuade token holders from voting in a particular way. These incidents have sparked discussions about private voting in the blockchain industry.
- Nouns DAO: which is partnering with Aragon. NounsDao have implemented an Aztec <> Aragon solution using Aztec’s zkDSL, Noir. This implementation enables anonymity and confidentiality of votes and outcomes, eliminating issues such as 11th-hour voting problems, vote coercion, and bandwagoning effects. The proposal utilizes Ethereum storage proofs and timelapse encryption for minimal off-chain dependency. The process involves three phases:
- Nouns Census using Ethereum storage proofs to prove ownership without revealing identities.
- Vote Obfuscation with Delay-Relayers to maintain privacy for multiple Noun holders, and
- Time-Lapse Encryption Service for tally fairness and aggregated vote decryption.
With this approach, Noun owners can prove ownership, maintain vote privacy, and cast votes securely and privately.
Cicada: is built to achieve running tally privacy in voting through the use of cryptographic primitives that have not been previously used on-chain. It leverages time-lock puzzles and homomorphic time-lock puzzles to enable secure and private voting without the need for tallying authorities or other trusted parties.
The design of Cicada aims to minimize trust and ensure censorship resistance in a blockchain context, making it a practical and efficient solution for private voting on-chain.Time-lock puzzles allow ballots to be submitted as encrypted puzzles that can only be revealed after a predetermined time, ensuring confidentiality during the voting process.
To prevent vote manipulation, voters must submit zero-knowledge proofs of ballot validity alongside their ballots. Cicada also offers the option to combine with an anonymous voter eligibility protocol for indefinite ballot privacy.
Private Gaming
There’s undeniable growth in scaling solutions for on-chain gaming. But, once again, the majority of these solutions only use the succinct properties of SNARKs. However, there’s a use case for the gaming industry to add the privacy properties of ZK to their stacks, which could avoid transaction frontrunning and improve the user experience.
Dark Forest: is a mythic game that uses ZKPs for privacy, is a fully decentralized and persistent real-time strategy (RTS) game built on Ethereum.
• The game leverages zkSNARKs, to create a cryptographic fog of war, enabling players to keep their planet locations and moves private.
• Players submit commitments and zero-knowledge proofs, proving the validity of their actions without revealing the actual locations.
• Players cannot inspect the contract to gain information about their opponents, creating an incomplete information game setting with strategic depth and emergent player behavior.
Private DeFi
Another space where privacy is needed is DeFi. On Ethereum, there’s a growing niche of Private DeFi apps.
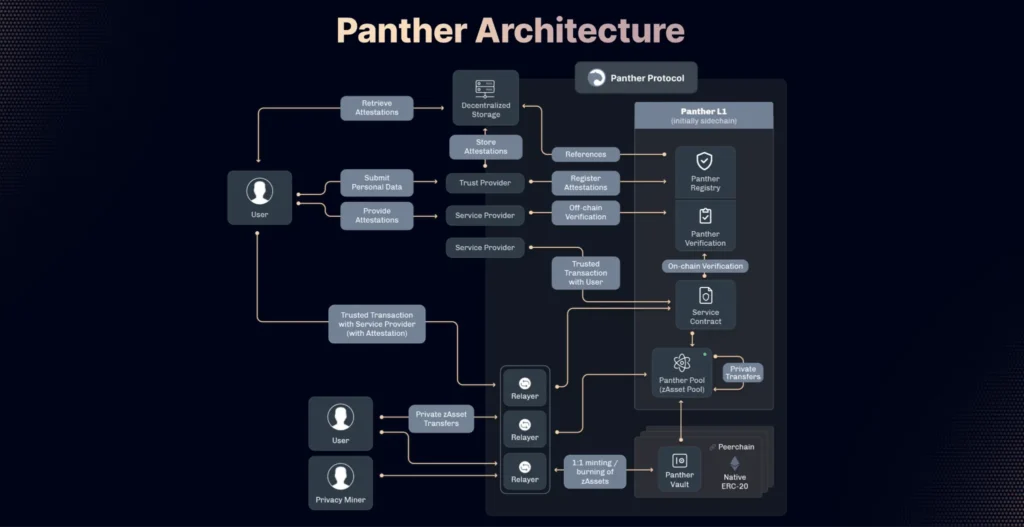
Panther Protocol: provides users with interoperable, fully collateralized digital assets that leverage zkSNARK technology. It also offers a novel price discovery mechanism for privacy. Users can mint zero-knowledge zAssets by depositing digital assets from any blockchain into Panther Vaults and use these zAssets across various DeFi applications.
Railgun: utilizes zkSNARKs to enable private smart contract calls directly on-chain, without relying on a separate Layer-2 validator set or a custodial bridge.
• By keeping funds within the host chain, Railgun ensures higher security and airtight privacy, preventing information leakage or contamination.
• Railgun’s privacy capabilities have potential use cases including private payroll services, MEV advantage for traders, censorship-resistant donations, anonymized analytics, and compliance with data protection laws.
ZK ML
One benefit of using zkSNARKs with Machine Learning algorithms is the ability to conduct Inference on Private or Sensitive Data while maintaining privacy. Our Q2 2023 State of ZK Report highlights the role of ZK in preserving privacy.
• ZK proofs allow for running machine learning inference on private or sensitive data while proving the accuracy of computations without exposing the data itself.
• Current ZK systems may not be suitable for such a system and future Fully Homomorphic Encryption (FHE) schemes may be better suited. At the moment, there are no live privacy preserving ZK solutions for ZKML algorithms.
Conclusion
Ethereum has a strong and active community focused on privacy. However, due to the increased emphasis on scalability, privacy has taken a backseat. We will likely see advancements in decentralized identifiers (DIDs) and gaming before DeFi or on-chain voting because the former two use cases stand to benefit significantly from robust privacy measures to make their value proposition viable.
Ethereum Privacy Ecosystem