A survey on ZK IDs
Introduction
A survey on ZK IDs
We explore the projects building ID solutions using Zero Knowledge Proofs.
Intro
When it comes to privacy, identity is a key concern. In today’s digital age, personal data is constantly being collected and shared, making it imperative to ensure the security and control of one’s identity. However, traditional centralized systems for managing identities have vulnerabilities that make individuals susceptible to data breaches and surveillance. Fortunately, there is a promising solution that has gained significant attention: the use of Decentralized Identifiers (DIDs) combined with Zero Knowledge Proofs (ZKPs).
In the following paragraphs, we will first examine the various types of identities by creating a comprehensive taxonomy. Then, we will delve into some of the projects that aim to address the challenges that have hindered the growth of decentralized digital identities in the past.
What types of IDs are out there?
In order to effectively manage identity, it is important to understand the different types that exist. Identity can be divided into two main categories: physical identity and digital identity. Physical identity refers to a person’s tangible characteristics, while digital identity is related to their online presence.
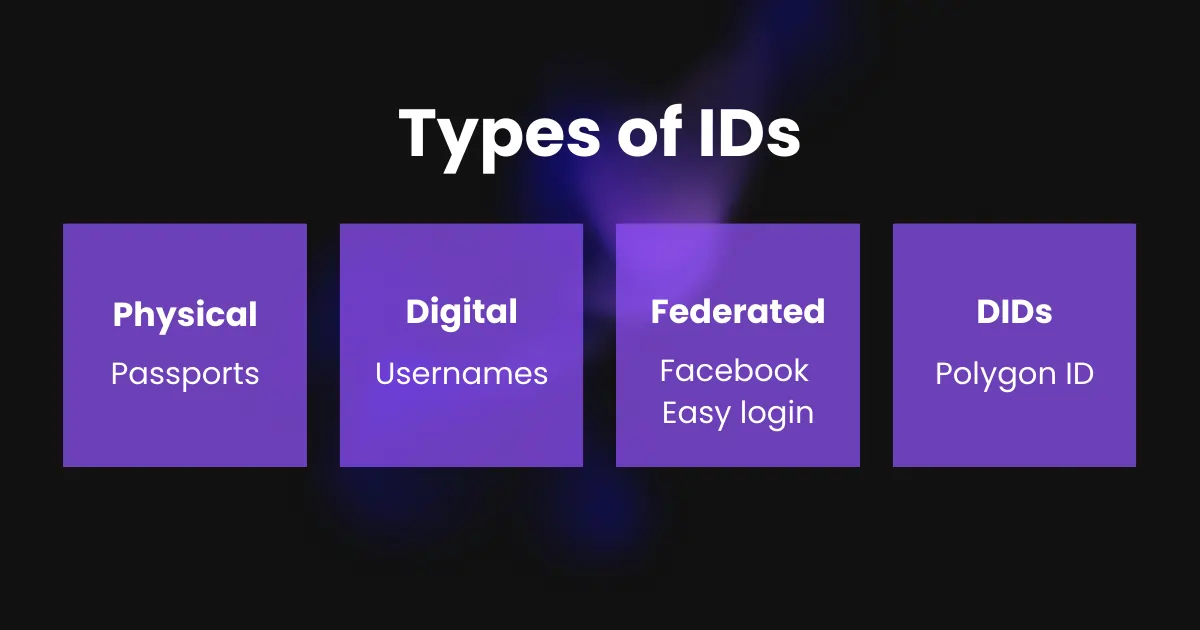
Physical identities refer to tangible documents like passports, driver’s licenses, and diplomas, while digital identities encompass a broader spectrum of identity management in the digital realm.
Digital identities can be further classified into subgroups that have evolved. The initial phase witnessed the emergence of siloed or centralized identities. These identities are characterized by website-specific login credentials, where each website or application has its own username and password requirements.
Federated identities marked the next stage in the evolution of digital identities. This approach aims to simplify the user experience by offering a single set of login credentials that can be used across multiple websites or applications. Users can leverage well-established identity providers like Facebook or Google to authenticate themselves without needing separate credentials for each platform.
However, our discussion focuses on the most recent advancement: self-sovereign or decentralized identities.
Self-sovereign identities give individuals complete control over their data. Unlike centralized and federated identities, where the identity provider holds and manages the user’s data, self-sovereign identities enable individuals to store their data on personal devices and share it selectively when necessary.
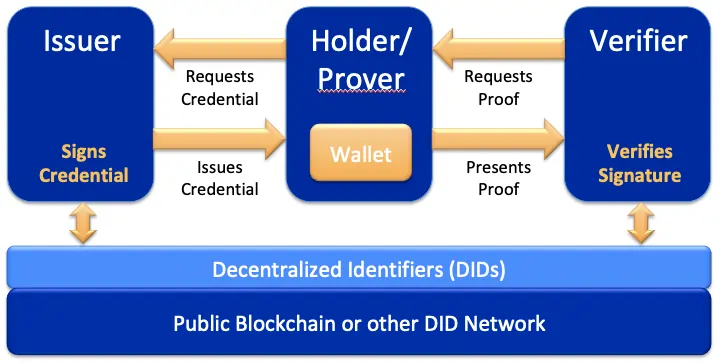
This shift towards self-sovereign identities aligns more closely with the concept of physical identities. Users have ownership and control over their digital identity, much like they possess physical documents such as passports. The ability to present specific claims from their digital identity, instead of revealing the entire record, offers heightened privacy and data control.
As with any form of identity, there are pros and cons associated with each type. Physical identities can be lost, forged, or forgotten, while digital identities face risks such as data breaches and reliance on centralized or federated providers. Centralized identities may restrict data portability, and federated identities expose user information to identity providers. In contrast, self-sovereign identities give users control, privacy, and the convenience of digital identity management.
Who’s building IDs with ZK?
In the following lines, we will explore the main projects that use Zero Knowledge Proofs to improve privacy and management.
Sismo – solving the Single Sign-on problem
Sismo is a platform that leverages zero knowledge proofs (ZKPs) and privacy-preserving technologies to offer users enhanced control over their personal data. At the core of Sismo’s solution is Sismo Connect, a seamless single sign-on (SSO) mechanism that enables selective disclosure of personal data to applications without compromising privacy.
The SSO proposal by Sismo
Sismo Connect is a privacy-centric alternative to traditional non-sovereign SSOs like “Sign in with Google” or limited SSOs such as “Sign in with Ethereum.” It allows applications to request access to personal data without directly accessing sensitive user information. By utilizing Sismo Connect, users can aggregate their identity in their Data Vault, an encrypted storage for personal data from various web2 and web3 accounts, credentials, and attestations.
Within the Data Vault, users can store granular pieces of data known as Data Gems, which represent valuable elements of their digital identity. For example, Data Gems can include entries in registries, platform contributions, or specific demographics. The Data Vault is a private and secure repository that provides users complete control and ownership over their aggregated digital identity.
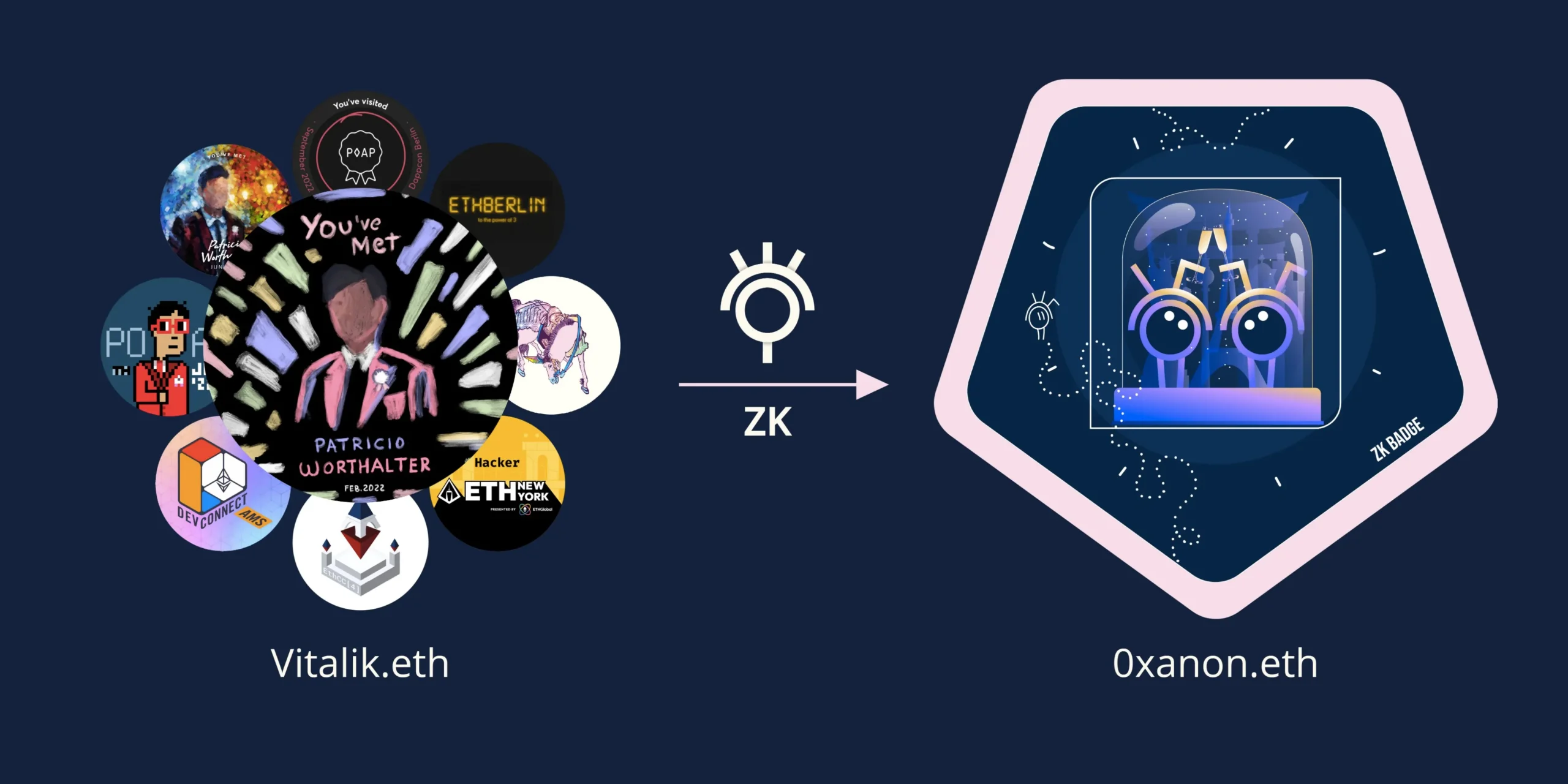
Using Sismo’s communication protocol, users can prove ownership of Data Gems by generating zero knowledge proofs. Proving schemes based on ZKPs allows users to verify ownership of specific data without revealing sensitive details, ensuring privacy in the process. Applications integrated with Sismo Connect can accept and verify these proofs, enabling users to selectively disclose Data Gems without compromising the privacy of the associated Data Sources.
Developers can integrate Sismo Connect into their applications, granting access to a wide range of user data from both web2 and web3 sources. By implementing Sismo Connect, applications can offer enhanced functionalities such as access control, reputation importation, and personalized experiences while preserving user privacy through selective disclosure.
Polygon ID
Polygon ID’s architecture combines identity state on-chain and off-chain elements, along with the implementation of zero knowledge proofs.
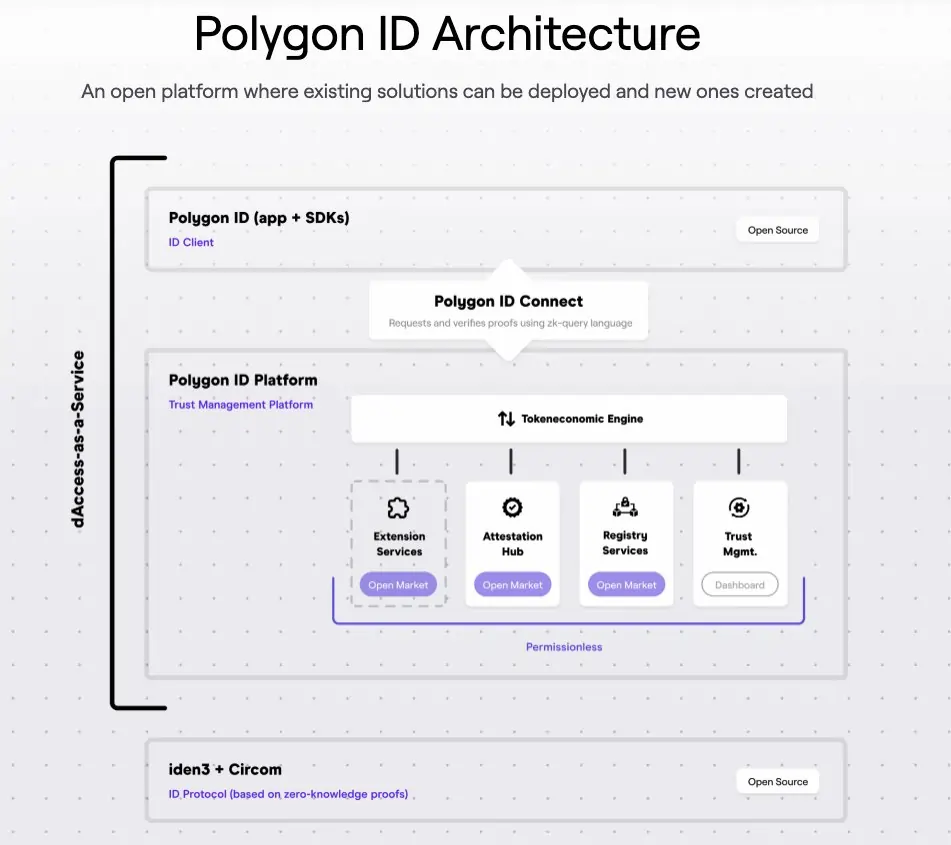
The Architecture of Polygon ID
At the core of Polygon ID is the concept of identity state, which is a commitment published on the blockchain. The identity state comprises three Merkle trees: the claims Merkle tree, the revocations tree, and the roots tree.
The claims Merkle tree stores individual claims, each with its own schema, identifier, and additional fields. This tree enables efficient retrieval and verification of claims, mapping specific information to corresponding claims.
The revocations tree stores revocation proofs for claims that have been invalidated. When a claim needs to be revoked, the issuer adds revocation proofs to this tree. By referencing the appropriate revocation proof, the validity of a claim can be easily verified.
The roots tree serves as a historical record of the identity state. Updated roots are added to this tree whenever new claims or revocations are made. It allows for the validation of different states and ensures that proofs can be generated using the latest state of the identity.
Claim Issuance and Verification
Users interact with the Polygon ID system to obtain and utilize claims. For example, a university issuing a diploma acts as an issuer. When the university issues a claim, it is added to the claims Merkle tree and signed with a digital signature. The user receives the claim, the corresponding Merkle tree proof, and the digital signature.
To utilize the claim, the user provides the necessary proofs and signatures to relevant verifiers, such as potential employers or applications. The claim can be used immediately with just the digital signature or published on-chain for additional properties that come into play. Verifiers can then validate the claim’s inclusion in the Merkle tree, prove its uniqueness, and verify that it has not been revoked.
What role does Zero Knowledge (ZK) play in this?
Zero knowledge proofs are vital in enhancing privacy and enabling efficient verification within the Polygon ID system. Users generate zero knowledge proofs to demonstrate the validity of their claims without revealing sensitive information. The zero knowledge circuit receives inputs, including public inputs and private inputs.
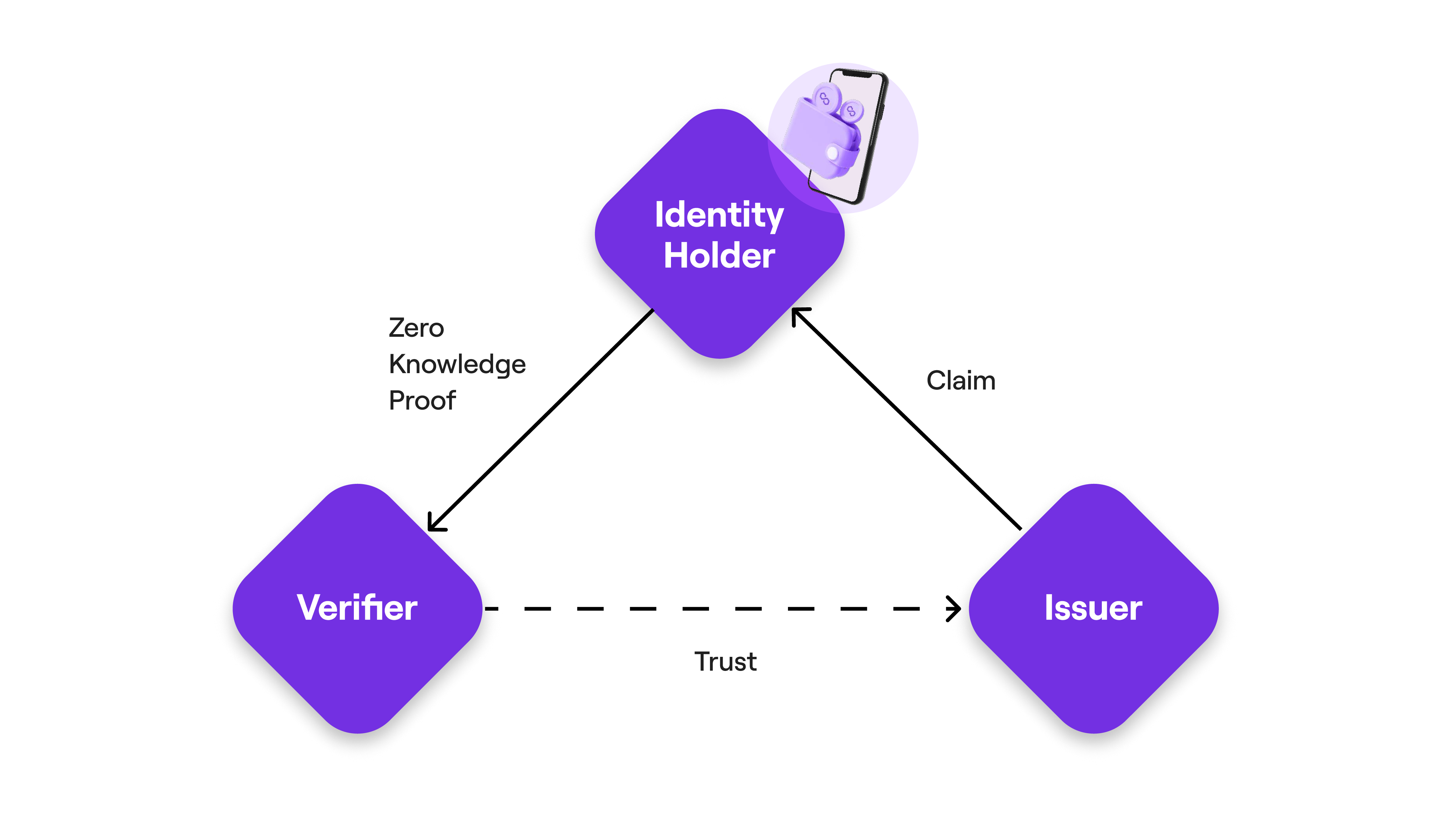
Public inputs include data necessary for verification, such as the age requirement or specific claim types. Private inputs consist of the claim itself, along with Merkle tree proofs and revocation proofs. These private inputs prove the claim’s authenticity and ensure the absence of revocations.
By generating zero knowledge proofs, users can verify their claims against the public inputs and provide the resulting proof to verifiers. Verifiers can validate the claim’s authenticity without accessing the underlying data or compromising user privacy.
Ensuring Correct State Transitions and Privacy
To maintain the integrity of the identity state and prevent unauthorized modifications, Polygon ID employs zero knowledge proofs for state transition verification. Issuers generate zero knowledge proofs to prove that they have correctly updated the identity state. These proofs confirm that issuers have followed the predefined rules and have not tampered with the state.
This approach provides a robust mechanism to ensure privacy and security in identity state transitions. Complex rules and operations can be defined within the zero knowledge circuits to validate various aspects of the claims, such as age requirements or specific conditions. Users can prove compliance with these rules without revealing the underlying data or compromising their privacy.
Holonym
Holonym serves as an identity bridge and mixer, cloaking off-chain credentials and making them available on-chain for various web applications. This combination of composable ledgers, privacy-enhancing techniques, and zero knowledge proofs unlocks a range of use cases. These include on-chain identity verification, Sybil resistance, digital crime prevention, and noncustodial wallet recovery. While these features benefit the web3 ecosystem, they also have the potential to enhance security and privacy in the wider internet landscape, mitigating crime, Sybil attacks, and data leaks.
The Process of Identity Verification and Anonymization
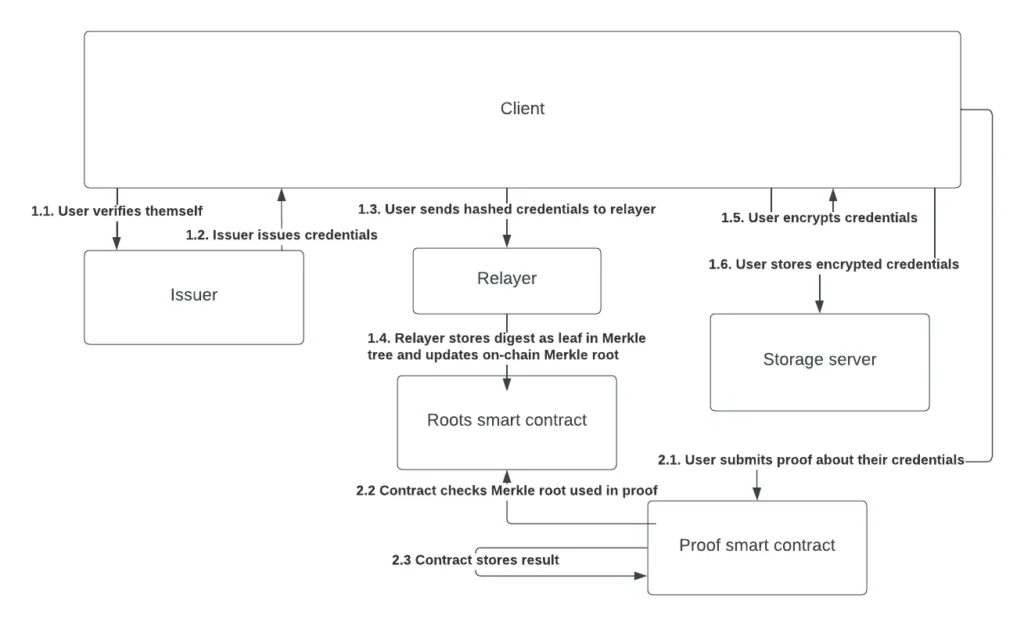
An issuer verifies a user’s identity and provides a signed credential. To protect user privacy, the user generates a commitment of their signed credentials, replacing the secret with a random value unknown to the issuer. This commitment is then submitted to the Merkle tree. Users can subsequently prove various statements about their Merkle tree element without revealing sensitive information.
ZK-Friendly Credential Format
To enable decentralized and private attestation and proving, credentials need to be properly formatted. Holonym proposes a credential format that is compatible with efficient hashing algorithms like Poseidon. The format includes mandatory fields such as issuer (the credential issuer’s Ethereum address) and secret (used as a nullifier and pepper). Additional fields can be included as optional elements, allowing flexibility in representing different attributes.
Checking and Modifying Commitments
Before adding commitment to the global Merkle tree, the validity of credential commitments must be determined. The issuer signs valid credentials, and the commitment includes a secret unknown to the issuer. The process involves several steps:
- Issuer returns verified credentials, generates a commitment, and signs it.
- The user replaces the secret with a random value unknown to the issuer.
- The user commits to the credentials with the new secret.
- The user generates a ZK-SNARK proof, demonstrating that the new commitment and old commitment derive from the same preimage but with a different secret.
- The Holonym smart contract verifies the ZK-SNARK proof.
- The smart contract checks the old commitment’s signature against the issuer address provided in the ZK-SNARK, ensuring credentials originated from the issuer.
- The smart contract checks that the old commitment hasn’t been used before, preventing double-spend attacks and Sybil attacks.
- The valid new commitment is added to the Merkle tree.
Proofs of Attributes
Once the credential commitments are part of the on-chain Merkle tree, users can prove facts about their credentials from any wallet address using their secret. Proofs of attributes are facilitated through ZK-SNARKs, which include sets of credentials. The proof demonstrates the inclusion of the credential hash in the Merkle tree and verifies specific properties, such as validating a country code.
Proving Ownership of Web2 Accounts
Holonym can also facilitate the proof of ownership of Web2 credentials. Verification of JSON Web Tokens (JWTs) within a SNARK is employed for this purpose. The system forwards web tokens to smart contracts, which verify the authenticity of the token’s data by checking if it is signed by the respective OpenID provider, such as Google for a Gmail account.
Manta SBT
The zero knowledge Soulbond Token (zkSBT) developed by Manta Network offers enhanced security and privacy features compared to traditional Soulbond Tokens (SBTs). zkSBTs utilize zero knowledge Proofs (ZKPs) to enable secure and private minting while preserving ownership privacy. These tokens can be launched on various blockchain networks while maintaining privacy credentials on Manta Network’s chain, verified through Proof Keys without wallet disclosures.
zkSBTs are bound to a zkAddress, which serves as a reusable and auditable address for private assets in Manta. Each zkSBT is associated with a single zkAddress, and multiple zkSBTs can exist within one zkAddress. The metadata of zkSBTs, such as profile pictures, AI-generated images, social graph information, etc., can be included, providing flexibility.
One of the key technologies developed by Manta Network is the Proof Key, which allows users to verify their identity and ownership of zkSBTs on-chain without relying on wallet signatures. This feature simplifies mobile application integration and enables various verification use cases, such as privacy-preserving profile pictures, on-chain transactions without disclosing address information, in-game item ownership, and decentralized social graph information.
Etonec’s zkp-ID on Mina Protocol
Crypto payments company Etonec, in collaboration with the Mina Foundation, is set to launch a new regulatory compliance tool powered by zero knowledge (ZK) proofs. The tool aims to address privacy and compliance gaps in the decentralized finance (DeFi) and Web3 sectors. It will provide know-your-customer (KYC) and anti-money laundering (AML) services on the Lumina DEX, a decentralized exchange. The prototype utilizes zkApps technology to enable private and compliant transactions. By leveraging zero knowledge proofs, the zkp-ID solution ensures regulatory requirements without users having to share sensitive personal information. Etonec’s partnership with Lumina DEX will establish a permissioned pool that complies with AML regulations, potentially attracting institutional investors to the DeFi space. While initially focused on DeFi, the compliance tool aims to serve various applications across the Web3 landscape, allowing users to control their data privacy and decide with whom they share information.
Conclusion
One major challenge faced by DID solutions that incorporate ZK technology is the fragmentation of the blockchain industry. Currently, there is no interoperable solution that allows users to hold their ID on one network and use it everywhere. However, DID technology utilizing ZK is gaining traction among industry leaders. With the growing adoption of the Web3 space, we may be on the verge of a breakthrough for the industry. Companies like Sismo are taking steps in the right direction by bridging the gap between Web2 and Web3. Meanwhile, PolygonID appears to have the necessary technology and access to a large market to make DIDs a reality.