TL;DR ZK EthCC
TL;DR ZK EthCC
This is a wrap-up post with the highlights about ZK and privacy talks during the 2023 EthCC week in Paris.
EthCC: Evolution of Privacy on Ethereum
Let’s begin with the main event of this week that we commemorate annually. During EthCC, Anna Rose and Will Harborne, the creators of ZKValidator, shared their expert opinions on the past and future of privacy on Ethereum.
A bit of the history of ZK and Privacy
The origins of the Zero Knowledge (ZK) community can be traced back to 2017, when Zcash, a cryptocurrency focused on privacy, introduced innovative privacy concepts. These ideas quickly spread throughout the Ethereum ecosystem, sparking early hackathon projects aimed at incorporating privacy features.
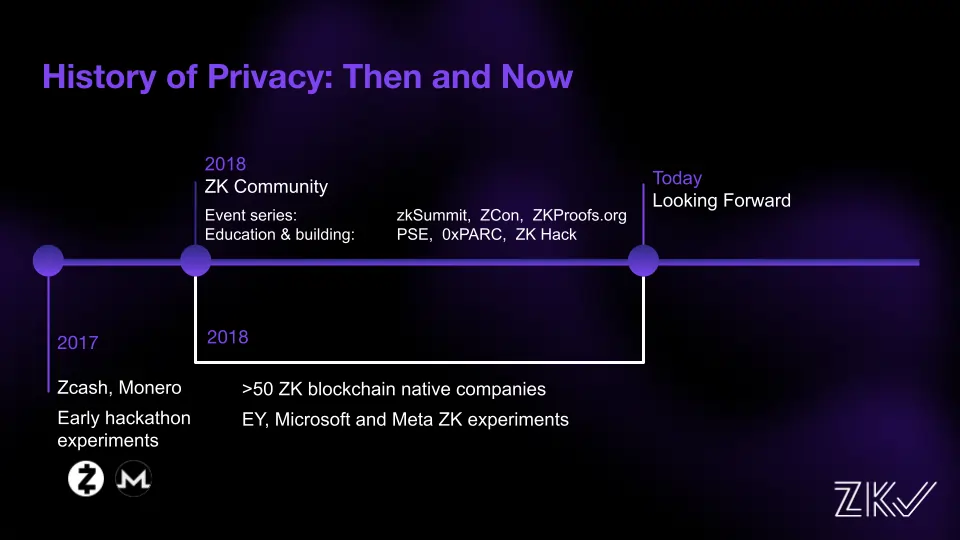
The ZK community was born during this time, with events like ZK Summit Series, ZK Proofs, and Z-Con, as well as the creation of shows like “Zero Knowledge”. This community has grown rapidly, leading to the development of over 50 companies focused on blockchain technology with a ZK approach. Major players like Microsoft and Meta have also joined the privacy movement and are conducting their own ZK experiments.
Privacy on Ethereum now.
The adoption of ZK technology has prompted many teams to add it to their stacks. However, it’s worth noting that several of these teams only use the SNARKs properties for scaling rather than the Zero Knowledge privacy feature of ZKPs.
As an example, we have:
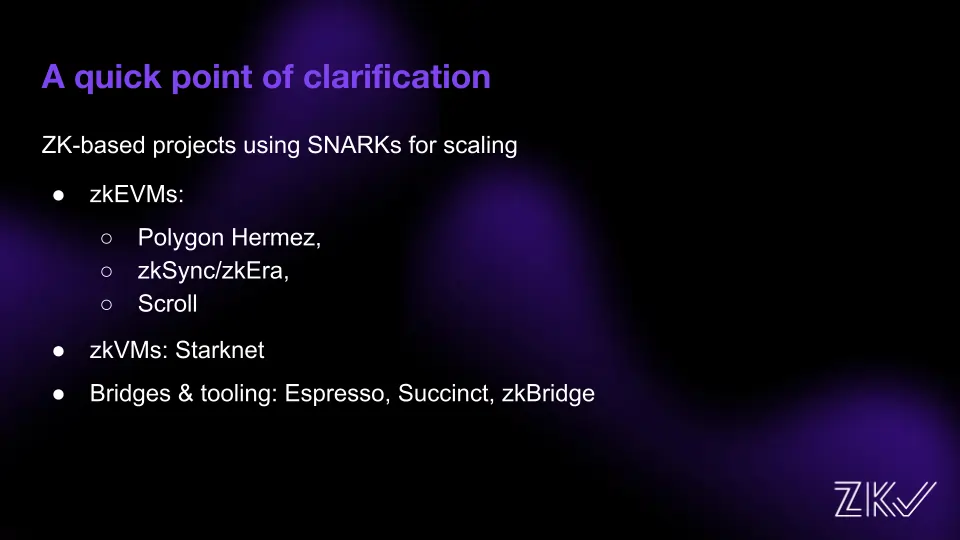
With that in mind, we can now move on to the privacy use cases on Ethereum.

The future use cases for privacy
Looking ahead, there are several potential areas for privacy expansion on Ethereum:
Privacy of Real-World Assets: Integrating real-world assets with on-chain data offers novel possibilities, especially in DeFi applications and beyond. Ensuring the privacy of these assets can revolutionize financial interactions on the blockchain.

Privacy-Preserving Tools: Advancements in cryptography, such as Fully Homomorphic Encryption (FH) and Multi-Party Computation (MPC), are key to unlocking new privacy use cases. These tools promise enhanced privacy protection for users while interacting with blockchain applications.
Specialized Hardware: Developing specialized hardware can significantly boost the efficiency and speed of ZK-based systems. Faster and more efficient privacy solutions will pave the way for broader adoption and usage.
Challenges and Opportunities
Despite significant progress in privacy adoption on Ethereum, there are still several challenges that need to be addressed. One of the primary concerns is ensuring legal and regulatory compliance, especially with recent sanctions and increased legal scrutiny. It is important to find solutions that balance privacy and compliance to create a favorable environment for privacy-based projects.
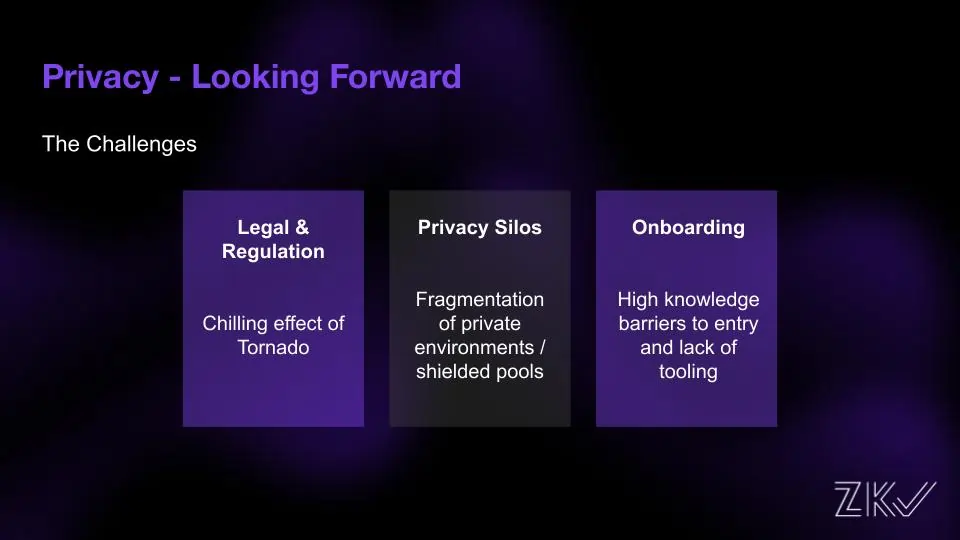
Another challenge is breaking down silos and achieving privacy by default. Although private applications exist, they often function in isolated ecosystems, which limits their widespread adoption. Encouraging interoperability between different privacy-centric solutions can promote a more cohesive and comprehensive approach to privacy on Ethereum.
Simplifying the user onboarding process is also crucial for driving adoption. Privacy-focused applications can be daunting for new users, and complicated onboarding experiences may discourage potential developers and users. Designing intuitive interfaces and providing seamless experiences can make privacy-centric solutions more accessible and user-friendly.
ZK Paris
During the EthCC week, the ZKValidator team joined forces with Geometry to fill an entire day with talks about the latest developments in Zero Knowledge. That resulted in ZK Paris, an event that brought together builders across the whole ZK space, including scaling, privacy, folding schemes, ZKML, and more.
Can’t We All Just Get Along, Kobi Gurkan
In his welcome speech titled “Can’t We All Just Get Along,” Kobi, the Head of Research at Geometry, shared a message of friendship and collaboration in the blockchain and crypto landscape. He highlighted how the space has evolved significantly over the last decade, going from a single application, Bitcoin, to a diverse array of possibilities on Ethereum.
Kobi emphasized the importance of cooperation, highlighted by various L2 solutions’ integration and usage of zk-SNARKs. He also mentioned exciting developments on the horizon, such as ZK composition, user-managed data, multi-party computation (MPC), and polymorphic encryption.
An Overview of Programmable Privacy, Lai Ying Tong
Zeromorph: Zero-Knowledge Multilinear Commitment Scheme, Tohru Kohrita
WGSL + Explorations, Koh Wei Jie
Koh Wei Jie’s talk focused on using WebGPU for crypto, aiming to address slow client-side zero-knowledge proof (ZK) generation. WebGPU is a new API for the web, supported by major browser companies, and it offers the potential to parallelize operations and accelerate computations on the client side. By leveraging GPUs, applications like matrix multiplication and private information retrieval can benefit from increased performance. Koh Wei Jie encouraged engineers and developers to explore this underexplored domain, emphasizing the need for developer tools, debugging tools, and security research. He presented moonshot ideas such as implementing ZK proofs, witness generation, and distributed proof generation networks using WebGPU for further advancement in the crypto space.
Modular Summit
It’s clear that modularity is a major focus in the blockchain space this summer, as demonstrated by the Modular Summit at EthCC. This event, organized by the Celestia team, brought together builders from various ecosystems to discuss a future where tools and layers are accessible to everyone, regardless of their stack.
As curators of the ZK Track at the summit, we were privileged to showcase projects that enable teams to build modularly using the power of Zero Knowledge Proofs. In this article, we provide a summary of the ZK Track.
Bonsai: a Verifiable & ZK Computing Platform for a Modular World
Brian Retford, CEO at RiscZero, introduced Bonsai, a verifiable and ZK platform for handling massive computations in the blockchain ecosystem. Bonsai’s capabilities include proving computations, ensuring interoperability, and supporting collaborative tools. It is built on the RISC-V VM and allows efficient splitting of proofs into smaller chunks.
The main goal of Bonsai is to make advanced ZK and cryptographic features accessible to developers across different blockchains. The speaker showcased examples of applications, such as a central limit order book and a voting system, utilizing Bonsai to reduce gas costs significantly. They also highlighted partnerships with other projects like Layered and Sovereign SDK. A fascinating hackathon project also demonstrated the combination of authentication standards with ZK for biometric-based wallets, making cryptocurrency access more user-friendly. The talk emphasised Bonsai’s potential to enhance the blockchain space through its efficiency and collaboration-focused approach.
Write Code, NOT Circuits
The talk introduced Noir, a programming language designed to be ZK-friendly, resembling Rust but with modern semantics. Noir helps convert high-level programs into snark circuits efficiently. To create composable hybrid applications, Aztec supports both public and private states in the blockchain, allowing users to transact privately while maintaining transparency for the protocol. The process involves constructing kernel snark circuits that verify individual function calls, recursively generating proofs for a complete execution environment with encrypted state changes. This approach opens up various possibilities, such as private voting and decentralized governance.
Shielded Transactions Are Rollups
Henry De Valence delivered a talk on Penumbra, a private proof-of-stake L1 with an interchange shielded pool. He introduced the concept of shielded transactions as micro roll-ups, where certain state fragments are operated on, allowing the state transition to move off-chain through ZK proofs. De Valence discussed the challenge of late binding in shielded transactions and proposed a model for asynchronous ZK execution via message passing, pushing computation to the network’s edges. He also introduced Narsil, a sub-project focusing on creating personal roll-ups, allowing users to move their state off-chain securely. The talk provided insights into the potential applications and benefits of Penumbra’s approach in the blockchain ecosystem.
Aggregation is all you need
Uma Roy, co-founder of Succinct, discussed their solution for interoperability during her talk. They developed an Ethereum ZK light client called Telepathy, allowing seamless messaging between Ethereum and other chains and bridging information from consensus to execution layers. Additionally, they expanded their support to other consensus protocols like Tendermint and Grandpa to enhance the domains that can communicate through ZK light clients. Collaborating with Celestia, Succinct is building a ZK bridge to bring Celestia’s state to Ethereum. Their innovative approach involves a three-step proof pipeline that efficiently generates and verifies proofs for various consensus protocols. The ultimate goal is to achieve proof aggregation, reducing gas costs on Ethereum and enhancing overall blockchain interoperability.
Axiom: The first ZK coprocessor scaling data-rich applications on Ethereum
The EthCC week confirmed that the ZK space is one of the most rapidly expanding segments within the entire blockchain ecosystem. While scalability dominates much of the conversation, privacy continues to be a crucial use case for ZK. However, the industry must strive for greater innovation in this area.
Throughout our time at EthCC, we engaged in conversations with numerous community members and observed a surging interest in ZK. However, we also noticed a significant lack of knowledge about it. We firmly believe that with more educational events focused on the use cases of ZK, innovation and adoption will see significant growth.