ZKV explores Boundless
Introduction
ZKV explores Boundless
This is an interview with Jacob Everly, product manager at RISC Zero.
RISC Zero’s Boundless launch is set for February 25th. In the lead up to this major milestone, we had a chance to catch up with Jacob Everly, Product Manager at RISC Zero. He shared a look into the protocol and explained how it will accelerate the larger ZK ecosystem. Here is our interview:
Q: Boundless introduces a decentralised market for proof generation and verification. Could you walk us through the entire lifecycle of a proof request in the Boundless Market—from submission to verification on-chain?
A: The most comprehensive resource for understanding how a proof moves through the market is depicted in the picture below:
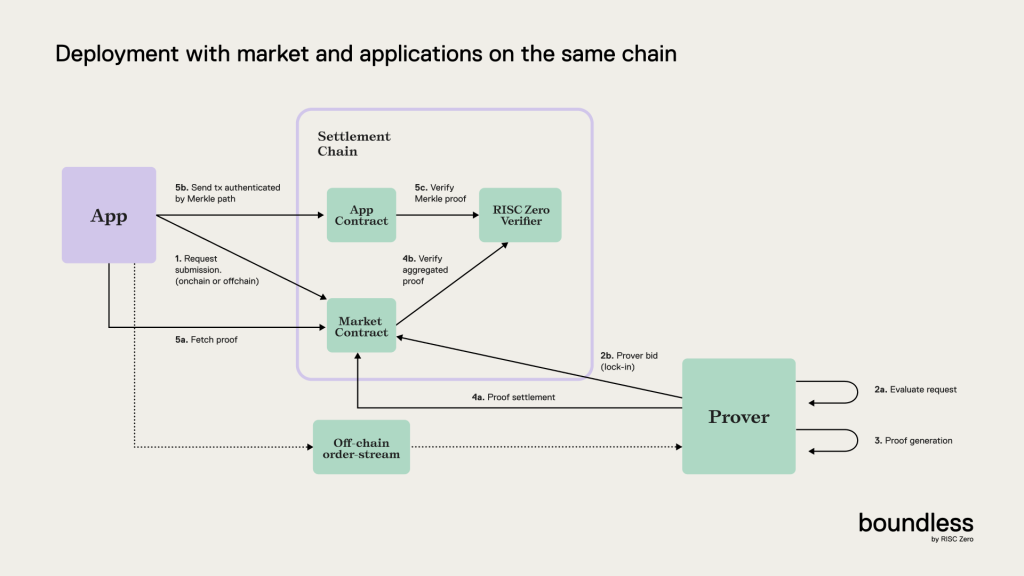 source: https://docs.beboundless.xyz/introduction/proof-lifecycle
source: https://docs.beboundless.xyz/introduction/proof-lifecycle
It is worth highlighting that we are leveraging native aggregation for streamlined proof handling. This ensures that multiple proofs can be efficiently combined, reducing redundancy and optimizing computational resources. Additionally, our system integrates automated verification, simplifying the process of trustless validation. We embrace open market dynamics to ensure that proof generation and validation operate in a competitive environment, guaranteeing users the best price for proofs.
What I am also excited about is that very soon Boundless will not only guarantee proof generation but also ensure reliable proof delivery directly to applications.
Q: The Boundless model emphasises combining on-chain and off-chain capabilities. Could you describe how the ZK coprocessor interacts with the EVM, and what are the key checkpoints during proof generation, orchestration, and on-chain verification?
A: With zero-knowledge (ZK) technology, the decentralization model shifts fundamentally—only a single party is required to ensure liveness, and no honest parties are needed for safety. This enables Boundless to offload traditionally on-chain components, significantly reducing the on-chain footprint while maintaining trustless security.
Boundless achieves all the necessary properties, delivering a complete request—including verification—for as little as 35k EVM gas!
Key checkpoints in this process include:
- Request – A proof request is initiated.
- Lock-in – The request is locked, ensuring a guarantee of fulfillment.
- Fulfill – The proof is delivered and verified.
These three stages can occur on-chain. Additionally, we offer off-chain requests to cut costs even further. Once a request is locked in, the application gains a strong guarantee that the proof will be delivered.
Q: Can you share how this would appear for the end-user? What would this enable for them?
A: For the end-user, Boundless introduces a seamless, developer-friendly experience that dramatically simplifies the ZK application deployment process. With the zkVM, we introduced a new paradigm: Write Rust → Generate ZKPs. Now, with Boundless, we take it even further: Write Rust → Deploy a production-ready ZK application.
This means that users only need to write Rust and configure a simple request in under 10 lines to launch a fully functional, production-ready ZK application—eliminating the complexity typically associated with ZK development.
And we’re not stopping here—more abstractions and expanded language support are on the way, making it even easier for developers to build and deploy trustless applications at scale.
Q: Recursive proofs allow Boundless to offer virtually unlimited compute capacity. How does this recursive proof mechanism work, and how does it enable parallelised proving for large-scale applications?
A: Boundless currently leverages the RISC Zero zkVM, enabling infinite horizontal scalability by utilizing multiple machines simultaneously.
We’re partnering with large data centers that can tap into their extensive machine infrastructure, benefiting from a low-cost electricity foundation to deliver scalable, cost-efficient performance.
Q: Proof aggregation is key to minimising on-chain verification costs. Could you explain how Merkle tree-based proof aggregation works and why it’s essential for efficiency at scale?
A: Proof aggregation enables us to generate a single proof that verifies the validity of multiple proofs at once! On Ethereum L1, verification can be costly—around $10 per proof. However, with Boundless’ native aggregation, applications can share verification costs, significantly lowering the overall expense.
Q: In your presentation during ZK Hack Montreal, you mentioned that recursive proofs could combine multiple rollup states into a single proof. How does this impact cross-rollup interoperability, and how does zkVM ensure atomicity and security across rollups?
A: To achieve atomicity across rollups, we must enable real-time proving. Real-time proving allows a proof to be requested and submitted within a single block on the settlement layer, ensuring that each bridge contract updates simultaneously for seamless cross-rollup interactions.
Q: In the context of proving historical state or external state, how does the zkVM handle proofs for external data sources, and what mechanisms ensure the integrity and consistency of such off-chain state?
A: With Steel, generating a state proof from any given blockhash is straightforward—even allowing us to trustlessly prove state all the way back to Dencun. For state data before April 2024, a trusted solution is needed to fetch the corresponding blockhash. But since Steel verifies blockhashes on-chain, any incorrect blockhash simply leads to a failed proof, ensuring absolute trustless integrity and consistency.
Q: Debugging and optimizing zkVM programs is often challenging. What tools or techniques does RISC Zero provide for profiling, debugging, and optimising Rust-based zkVM programs?
A: Debugging and optimizing zkVM programs can be challenging, but RISC Zero provides a robust set of tools to streamline the process. Our developer documentation includes comprehensive guides on profiling and optimization, featuring:
- Proof tooling for generating flame graphs
- Detailed insights into the performance characteristics of zkVM applications
To further enhance performance, we offer precompiles for commonly expensive operations, including:
- Keccak
- SHA
- RSA
- and elliptic curve operations
For debugging, developers can leverage standard Rust tooling, as our zkVM allows writing genuine Rust code, compiled with Cargo/LLVM. This ensures:
- Informative error messages for easier troubleshooting.
- Compatibility with standard Rust debugging techniques, making the development process more intuitive and accessible.
With these tools, RISC Zero enables developers to build, optimize, and debug zkVM applications efficiently and effectively.
Q: With the zkVM supporting arbitrary Rust programs, what are the key security practices developers should follow to prevent potential vulnerabilities in proof generation and on-chain verification?
A: zkVM applications are composed of two components: a “guest” and a “host.”
It’s important to note that only the guest’s behavior is enforced. Developers should assume the host may be potentially malicious, which makes applications involving time or randomness especially susceptible to design vulnerabilities.
Additionally, while the proofs themselves do not expose any information about the program’s inputs or execution trace, the proof generator still has full access to all internal details.
Q: Bonsai appears to play a key role in proving at scale. Could you describe its architecture, the underlying hardware optimisations, and how Bonsai manages concurrent requests during peak load?
A: Bonsai was the world’s first parallel proving system for zkVMs. Building on those insights, we are now developing the proving node for Boundless. This advancement allows anyone to scale proving operations across multiple machines, providing applications with the most efficient proofs when using Boundless.
Q: As Boundless matures, what new use cases do you anticipate emerging, particularly in areas like decentralized finance, gaming, and cross-chain infrastructure?
A: Boundless unlocks three key features:
Security
For the first time, a ZK application no longer relies on the trust of a single party. Boundless is fully decentralized from day one, designed to secure billions from the start.
Performance
ZK is the endgame. It empowers applications with limitless computation while delivering industry-leading UX and enhanced security. A single party can now operate at maximum speed, with every action mathematically verified for trustless assurance.
Universal Compatibility
Boundless is the first platform to support universal protocols, making it easier than ever to deploy applications across multiple chains.
Example: EigenLayer can extend staking services across multiple chains.
Example: Hashflow can enable cross-chain deposits seamlessly.
Q: Looking ahead, do you see zkVMs benefiting from specialised hardware such as GPUs, FPGAs, or even custom ASICs for proof generation? What impact could this have on performance and cost?
A: Binius combined with ASIC is considered the endgame for ZK proving. Binius alone can deliver up to a 10x performance improvement out of the box. When paired with accelerated hardware, it has the potential to achieve over a 30x improvement compared to current proof systems.
Q: Boundless represents a new paradigm for proof generation and off-chain computation. To accelerate adoption, are there key strategic partnerships in the pipeline, particularly with L1s, L2s, or enterprise players?
A: Boundless represents the complete decoupling of execution from settlement layers. Ultimately, all solutions pursuing this approach will adopt ZK proofs to verify ZK execution. While rollups are currently the primary partners, co-processors are expected to gain a larger share of the market soon, as the transition is more seamless for them.
Thanks again to Jacob Everly and the entire RISC Zero team for their help in putting this post together. Stay tuned for the RISC Zero’s Boundless launch happening February 25th!
Link to the event:
https://x.com/boundless_xyz
Website:
https://beboundless.xyz/
Socials:
https://x.com/boundless_xyz