What’s Cooking at Sui?
What’s Cooking at Sui?
At Sui Basecamp 2025, Mysten Labs presented updates to Sui’s cryptographic infrastructure. Topics included zero-knowledge tunnels, programmable encryption, post-quantum readiness, and cross-chain identity.
TL;DR
ZK tunnels extend state channels with off-chain execution and selective disclosure.
Time capsules enable delayed access to encrypted data.
Offline transactions use symbolic templates for minimal-bandwidth environments.
Post-quantum primitives and identity protocols address long-term security and interoperability.
Intro
At Sui Basecamp 2025, Kostas Chalkias of Mysten Labs laid out a roadmap of cryptographic infrastructure that pushes beyond conventional blockchain architecture. The focus has shifted from consensus mechanics and throughput to the composability of privacy, programmability, and resilience.
What follows is a detailed look at seven critical cryptographic advancements introduced in the talk, spanning from interactive ZK channels to post-quantum security.
ZK Tunnels and Stateless Execution Channels
Sui’s ZK tunnels represent a programmable generalisation of the Lightning Network concept, combining state channels with zero-knowledge proofs and arbitrary off-chain logic. Unlike traditional payment-focused channels, these tunnels are application-agnostic. A single opening transaction establishes a cryptographic handshake; interactions proceed off-chain, and the final closing transaction settles the state using a succinct validity or fraud proof.

This design eliminates latency and gas costs between participants during the off-chain session. It’s particularly relevant for applications requiring high-frequency interactions such as P2P gaming, localised commerce, and AI agent simulations. Tunnels can operate over local transports like Bluetooth or low-range radio, meaning they remain functional without internet connectivity. Notably, the model supports configurable privacy: transaction details can remain private until the tunnel closes or be selectively disclosed for regulatory compliance.
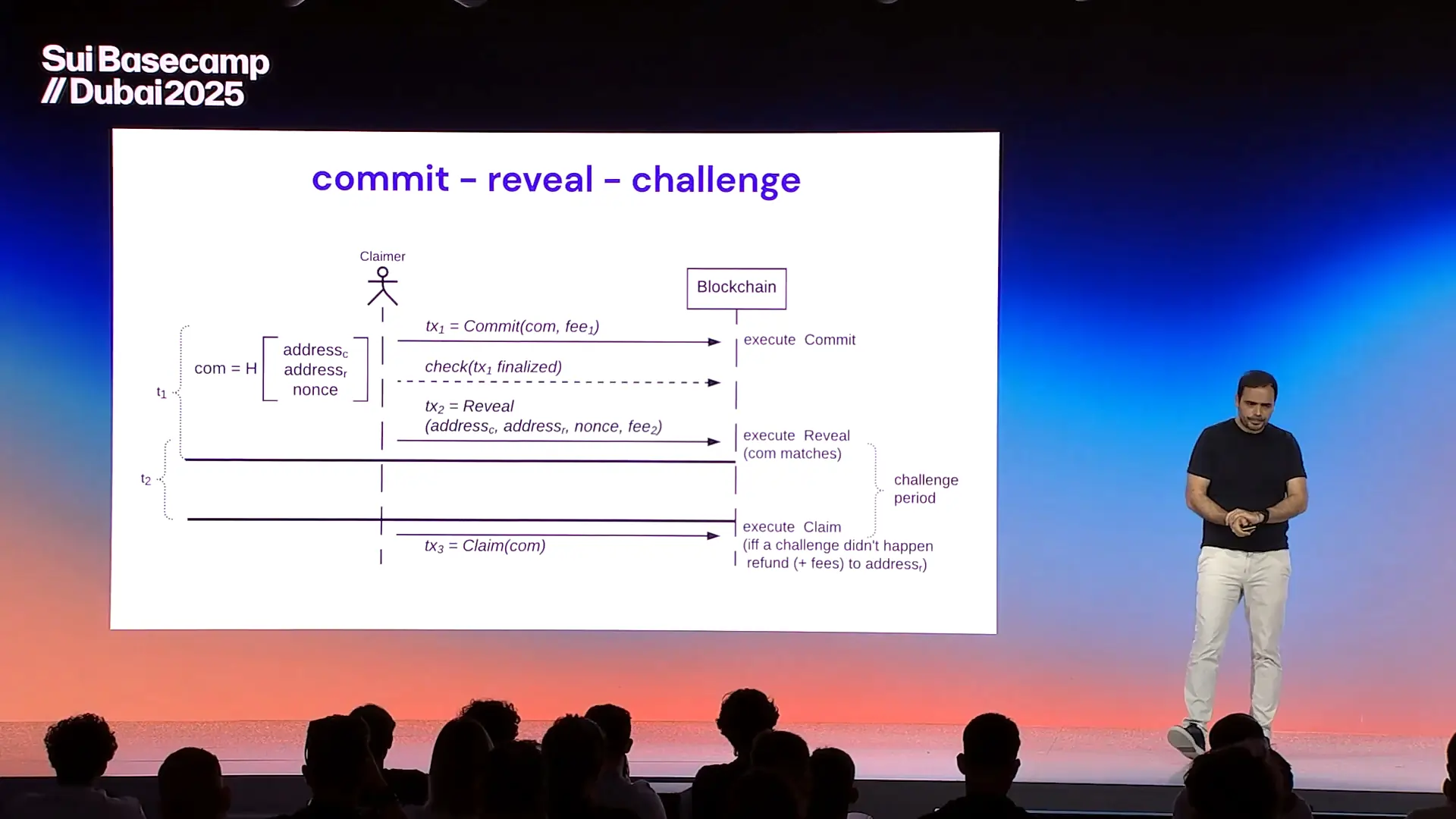
Time Capsules and Programmable Reveal Conditions
Time capsules on Sui introduce an encryption framework that enforces delayed access based on programmable time conditions. This allows for data or transaction logic to remain concealed until a predefined timestamp or event is met. Unlike simple timelocks, these capsules are integrated into Sui’s zero-knowledge infrastructure, enabling access delegation, selective disclosure, and composability with on-chain logic.
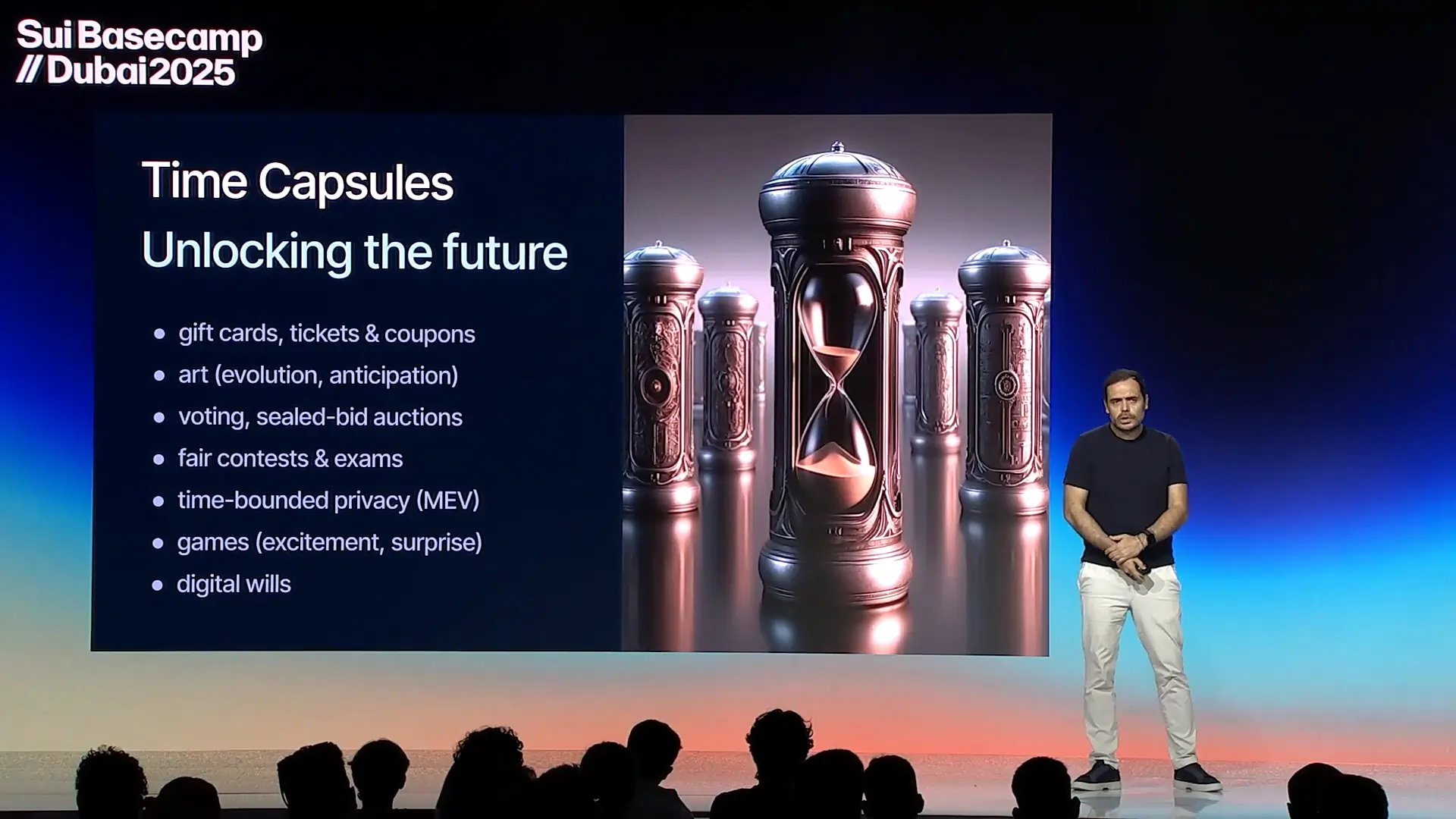
The implications span a range of domains. Auctions can operate in sealed-bid mode without relying on trust; freemium digital assets can incrementally reveal content post-purchase; legal instruments such as wills or corporate disclosures can be programmed to unlock based on inactivity or governance outcomes. These capsules also open a novel route to MEV resistance: transactions remain encrypted while in the mempool, only revealing their intent at execution time.
Offline-Capable Transaction Design
One of the more pragmatic developments is Sui’s move toward “internetless” transaction workflows. By compressing transaction intent into symbolic templates—essentially predefined mappings from input to action—a user can reduce a transaction to a few bytes. These are then signed and transmitted through minimal-bandwidth channels such as SMS, radio, or even audio.
The system relies on the deterministic verification properties of blockchain: even delayed or asynchronously delivered signatures can be validated once received. In a scenario where infrastructure is disrupted, such as natural disasters or network outages, users retain the ability to interact with the chain, purchase goods, or transfer assets. For devices and embedded systems, this model enables extremely lightweight blockchain interaction without full-stack connectivity.
Verifiable AI and Deterministic Agent Coordination
Sui’s cryptographic model provides the foundation for deterministic, auditable AI output. By seeding AI models with on-chain randomness and binding input/output pairs to verifiable proofs, Sui introduces the possibility of trustworthy AI interactions. This matters particularly in settings where reproducibility and auditability are critical—financial agents, competitive AI environments, or on-chain logic that depends on external computation.

When paired with ZK tunnels, this architecture creates isolated “arenas” where agents can operate under agreed rules, perform high-frequency interactions, and resolve outcomes in a verifiable manner. These interactions can span across inference boundaries—between LLMs, game engines, or robotic control systems—without sacrificing determinism or trust.
Post-Quantum Cryptography and Forward-Secure Primitives
Sui is transitioning toward a post-quantum secure stack in anticipation of the NIST 2035 mandate. This includes replacing traditional elliptic-curve signatures with lattice-based or multivariate schemes that offer quantum resistance. The engineering challenge here lies in minimising the on-chain footprint, as PQC schemes tend to have larger key sizes and slower verification.
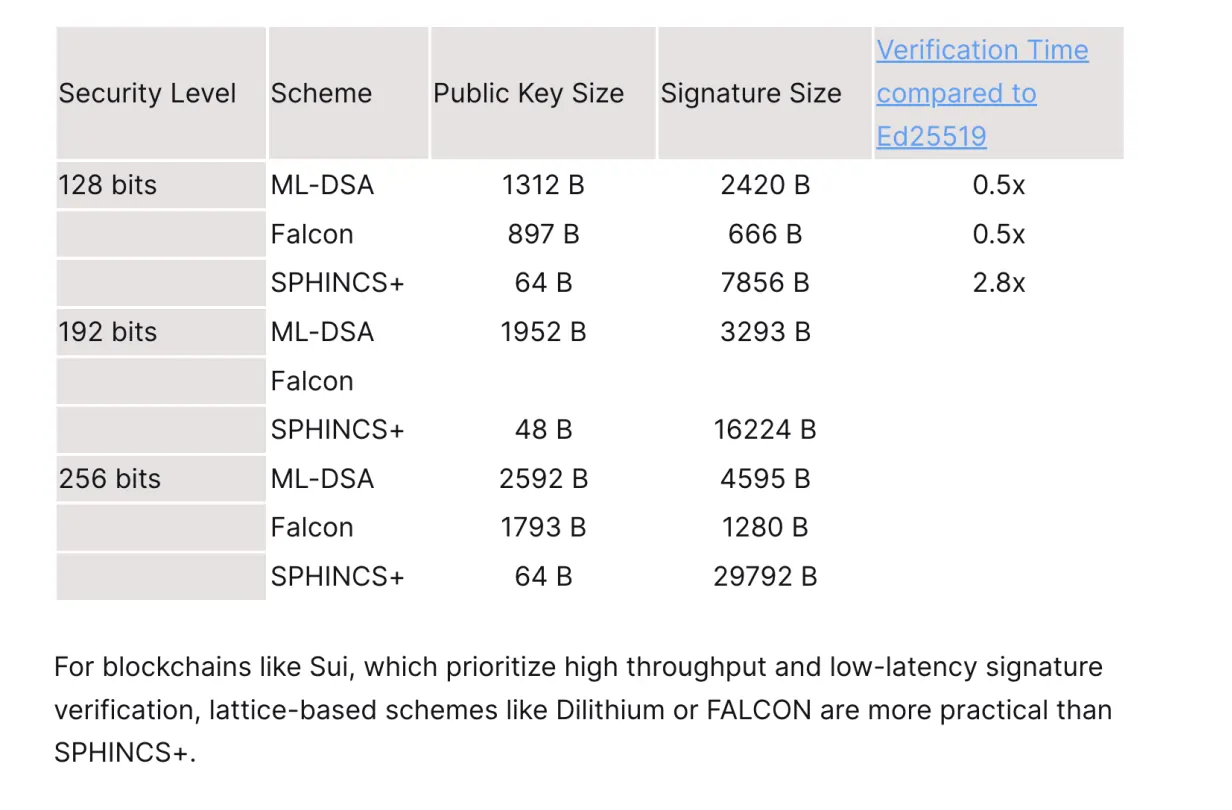
Efforts are underway to adapt zero-knowledge circuits and signature aggregation techniques to handle these constraints. Sui will offer progressive opt-in upgrades, allowing users and developers to migrate to quantum-safe addresses and assets over time. These primitives are already being tested in environments requiring forward secrecy and long-term archival guarantees, such as encrypted legal documents and digital wills.
Cross-Chain Identity and Signature Interoperability
With SUILINK, Sui introduces a native verification layer for signatures originating from Ethereum, Solana, and other ecosystems. This capability allows users to prove ownership of external accounts directly within the Sui runtime without involving wrapped assets or custodial bridges. A Solana user, for example, can sign a message using their Phantom wallet and claim rewards or access on Sui through direct cryptographic verification.
This is a foundational step toward practical multi-chain identity. It supports use cases such as cross-chain airdrops, decentralised identity federation, and migration of credentials or access rights. Developers can now build incentive structures that span networks without requiring trust assumptions outside cryptographic validity.
Recovery Logic and Verifiable Solvency
Two major cryptographic constructs round out the picture: key loss protection and solvency proofs. Reactive Key Loss Protection is a mechanism that lets users define on-chain logic for account recovery. If an account becomes inactive for a defined period, recovery agents (predefined keys or multisig arrangements) can regain control using zero-knowledge proofs and fraud-detection mechanisms.
In parallel, Sui is advancing the standardisation of solvency proofs for exchanges and custodians. By applying zkSNARKs over liability and asset tables, entities can prove solvency without disclosing individual user data. This mitigates the risk of collapses like FTX or Mt. Gox, while enabling real-time, user-verifiable audits.
Conclusion
The cryptographic systems presented at Sui Basecamp 2025 reflect an architectural direction focused on programmability, composability, and resilience at the protocol level. Features such as zero-knowledge tunnels, post-quantum signature schemes, and cross-chain identity verification suggest a trend toward addressing known constraints in current blockchain infrastructure—particularly around latency, privacy, and user recovery.
From a technical perspective, these mechanisms offer a set of primitives that may be useful for building applications with stronger guarantees around privacy, auditability, and availability in constrained environments. Their success will depend on continued implementation and standardisation, broader adoption, developer tooling, and alignment with regulatory frameworks.